Email Phishing en spoofing simulatiON
E-mail testing
Why an email test? For example, if you want to know the level of email knowledge of your employees and colleagues.
Email has become the common way to communicate. Unfortunately, in many emails, hackers’ bombs are hidden…
Do you recognize yourself in these questions?
Can I have an email test performed, with or without support?
Can an email start ransomware (hostage software)?
Is my computer well protected against emails with a virus?
How can an email put a virus in my computer?
Would an employee of my company fall for a phishing email?
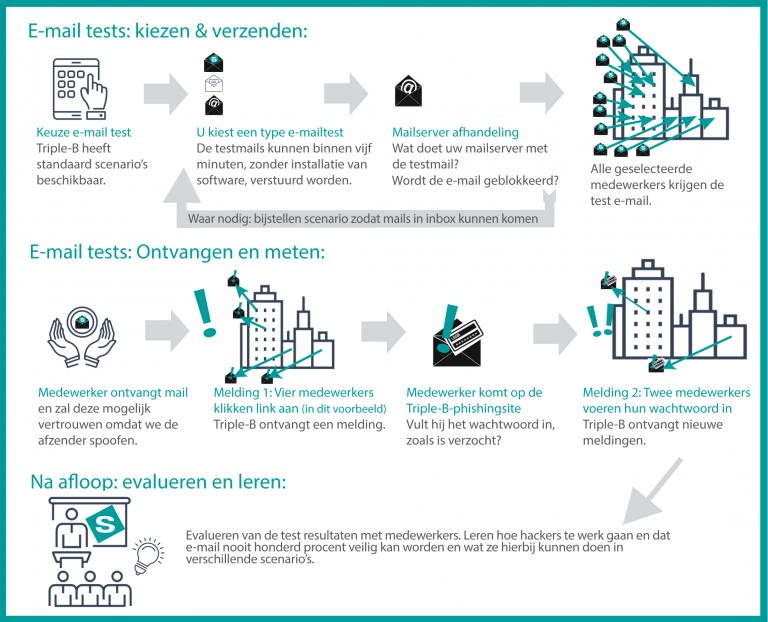
The email test:
Triple-B Consultancy has developed a handy and useful email test especially for this purpose. For these tests we have built our own platform with our own written software.
This software tests how well you are protected against ransomware and other attacks that can be used against your organization via email.
Our software can, for example, send a fake phishing mail through a fake identity with us to a specific email recipient within your organization. You can choose from the following options:
Phishing and spoofing test: we will send your employees a phishing email specifically aimed at obtaining passwords;
Spoofing link test: we send your employees a phishing email with the specific purpose of having a malicious link clicked on, without having to fill in the request for a password.
Test virus’: we send your employees a test virus in an email, which tests the security of the route to the user’s email program.
Test Macro virus’: we send your employees a macro virus, which is packaged in a word- or excel file and can be unpacked. It tests the safety of Office and the behavior of employees.
image test email’: we send a tracking image to an employee;
Integrity test mail: what do employees do with an email that tempts them to violate their integrity?
What do you get out of our email test?
Our experience is that Ransomware, in all cases that we have seen with our customers, arrived by email. We also saw phishing and other financial fraud often start with email. Sometimes hackers did that by putting an annoying link in the email, or by adding an attachment to the email.
With our email test you can test the hacking capabilities that hackers use. What types of mail still arrive at the workplace when you thought they might be blocked? And if the mail does arrive, what does your employee do with it? We test this for you with our test email scenarios of course without the test emails harming you. You will then know whether all workstations where mail is read are actually well secured and whether your employees would be wise in dealing with a suspicious mail or would fall into a trap of a hacker.
Afterwards, unless you don’t want to, the evaluation is included in the price. We will visit you on location and talk to the people tested about the risks of email, the reason why we do these kinds of tests and what an employee should or can do in case such an email arrives again. After all, the following mail can come from a real hacker.
How do you start our email test?
Are you interested in an email test? Then you can send an email to info@triple-b.net with the number of email addresses you would like to test. Or fill in the contact form on our website with the requested information. Indicate in the mail or contact form which of the above tests you want to perform and with what frequency. After approval of our quotation, we can start the tests within a day and sometimes within an hour. The planning is of course in consultation with you. Usually we involve an employee of the company in test scenarios 1 and 2 and sometimes 6. This person then becomes the ‘sender’ and has the task of keeping track of who contacts us and when, for example, to check whether the e-mail is real.
If confidential information is collected, it will be stripped by the software immediately during the test, so that we can never actually gain access to your passwords, for example. A hacker who uses similar techniques to steal your passwords will use or resell this confidential information.
Background information:
Explanation Phishing
Phishing is a widely used technique by hackers to obtain information from you or your colleagues. A common method is to build a fake website where the victims then enter their passwords. Our server also has these kinds of pages where we try to lure your employees with links to.
Consequences of a successful phishing attack
If a hacker has successfully carried out a phishing attack, the gateway to your company data is usually open to the hacker. Sometimes a hacker himself will penetrate your computers, but because so many people are still kicking in phishing attacks, large lists of passwords are usually collected and sold for a lot of money.
Explanation Spoofing
Spoofing means imitating someone’s identity or digital data in many ways. In an email test, spoofing means that we send an email from our own email test system, but to the recipient it looks as if the email comes from a friend. Their screen shows the sender’s email address and the name of another person. Unfortunately this is very easy to do with email, that’s why it’s used so much by hackers. Spoofing usually aims to increase the level of trust so that the recipient will follow the hacker’s instructions sooner. An instruction can be: “I’m the ict administrator, just click on the link for me,” or “Jannie’s salary has to be paid into this account next month.”
Consequences of spoofing:
Because employees of your company trust a spoofed mail from a hacker before, there is a chance that your company will be hacked. This can result in your secret information being divulged to the street, or a computer system being sabotaged or made unreadable. Usually you will be asked to pay a large amount of money to the hacker in bitcoins. It is also possible that spoofing money ends up in a wrong account, which is then called “Jannie’s account” but is actually a hacker’s account.
Explanation Ransomware:
Ransomware is the name for a type of virus that can ‘hostage’ your computer, server or database. This is why it is also called hostage software.
With many viruses, including ransomware, the trend is that the attack techniques become smarter and more and more different hacking techniques are combined. The Wannacry ransomware virus, for example, was responsible for enormous damage. The first step during the attack was probably an email containing the malicious virus. Once the virus had entered an internal network, because an unsuspecting employee opened an attachment, it could spread completely independently via a security hole in the network connection of all internal computers.
Did your organization create its own servers, data files or software, or have them created? Then it’s good to know that new types of Ransomware sometimes quietly encrypted and decrypted for months on end, so that all backups are also encrypted. After that, the hacker suddenly turns off the decrypt program remotely, so that all backups are “held hostage” as well.
Consequences of ransomware:
With ransomware, the hacker’s goal is always to get a ransom for “hostage” files. For the victim, however, it is uncertain whether the hacker will actually return the files after payment.
Ransomware can have enormous consequences, it can shut down all computers and servers of a company, and sometimes even several companies over several countries.
An informative article about the five known ransomware attacks can be read at https://www.csoonline.com/article/3212260/the-5-biggest-ransomware-attacks-of-the-last-5-years.html
Triple-B Consultancy has seen the consequences of Ransomware for its clients as well. Some companies were insufficiently secured and lost data permanently.
Nowadays, when personal data are lost, it is a legal obligation to report a data breach to the Dutch Data Protection Authority (Autoriteit Persoonsgegevens), with potentially unpleasant consequences in the area of finance and reputation. So prevention is better than cure.
Investigate how easily ransomware could cause damage to you by means of our email test.
